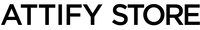Advanced Android and iOS Hands-on Exploitation is a unique training which covers security and exploitation of the two dominant mobile platforms - Android and iOS. This is a two day action packed class, full of hands-on challenges and CTF labs, for both Android and iOS environment.
The entire class will be based on a custom VM which has been prepared exclusively for the training. The training will take the attendees from the ground level upwards to be able to audit any real world applications on the platforms.
Some of the topics that will be covered are
- Advanced Auditing of iOS and Android Applications
- Reverse Engineering, Bypassing Obfuscations
- Debugging Android and iOS applications
- Runtime manipulation based attacks
- Automating security analysis, Exploiting and patching apps
- ARM Exploitation
- API Hooking and a lot more.
The online class is designed in a CTF approach where each of the module is followed by a complete hands-on lab, giving the attendees a chance to apply the knowledge and skills learnt during the class in real life scenario.
Students will also be provided With slides, reference materials and handouts to be used during and after the training class, and private scripts written by the trainer for Android and iOS app security analysis.
COURSE OUTLINE
Getting started with Android Exploitation and Pentesting
- Introduction to Android Security
- Android Debug Bridge 101
Android Exploitation 101
- Android Application Reverse Engineering
- Patching Android applications
- Hardcoding based vulnerabilities
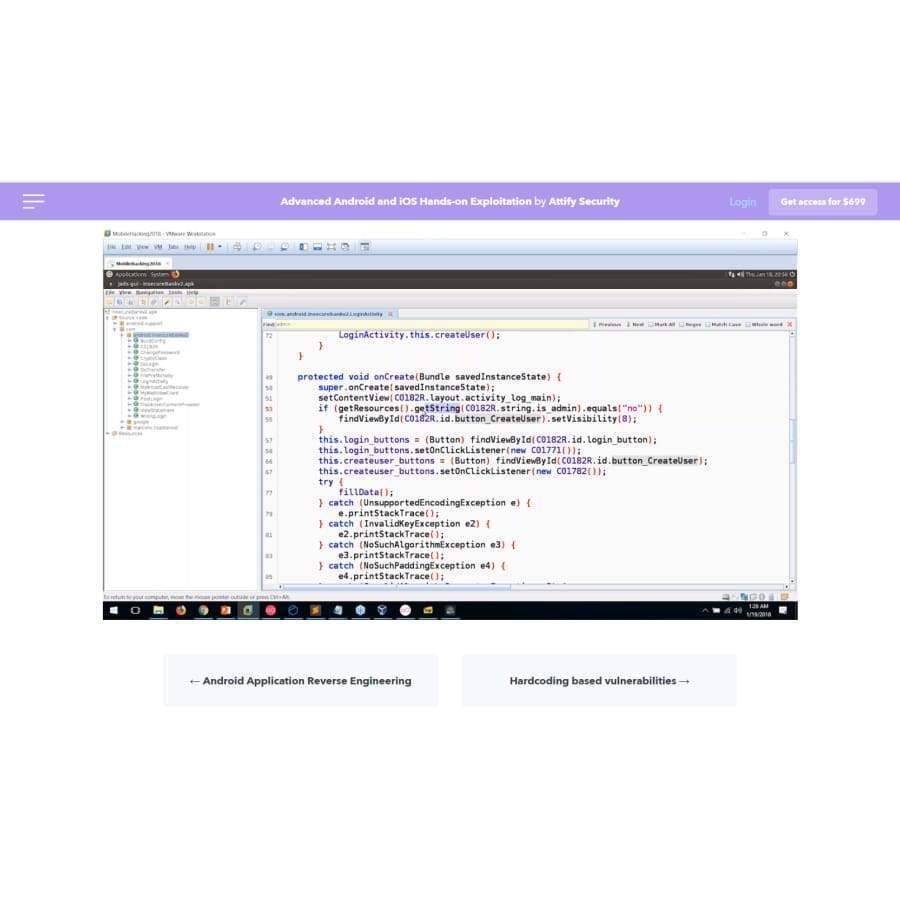
- Working with Unity apps
- Logging Based vulnerabilities
- Securing Android components
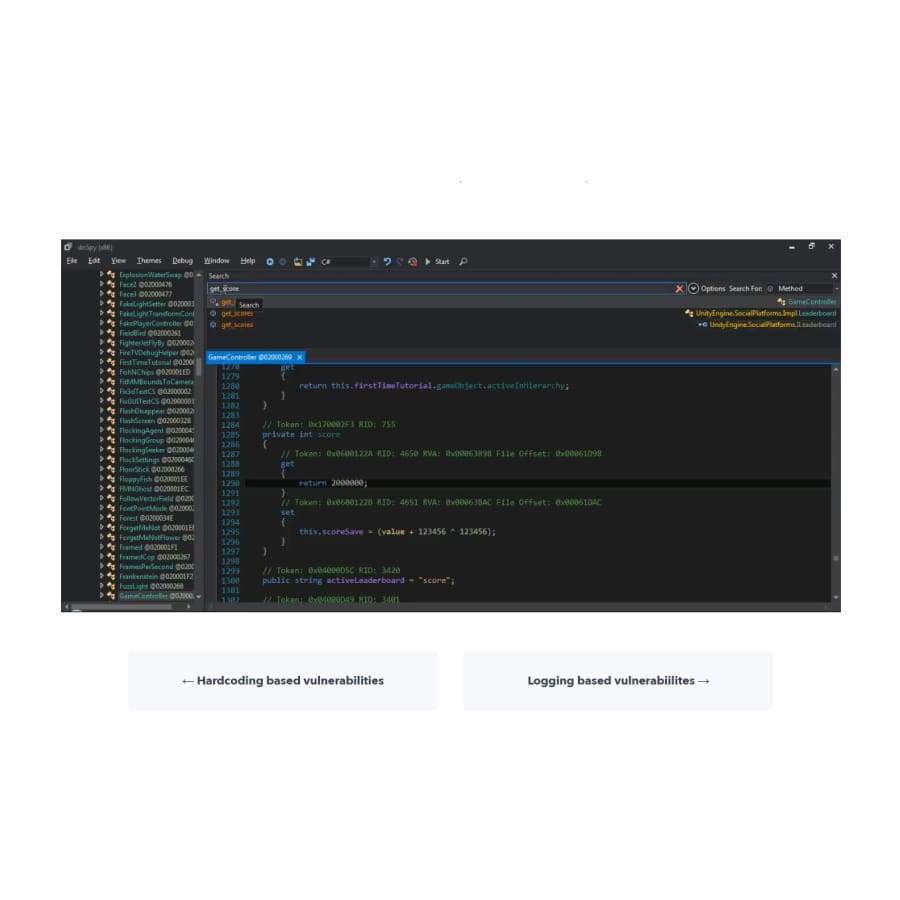
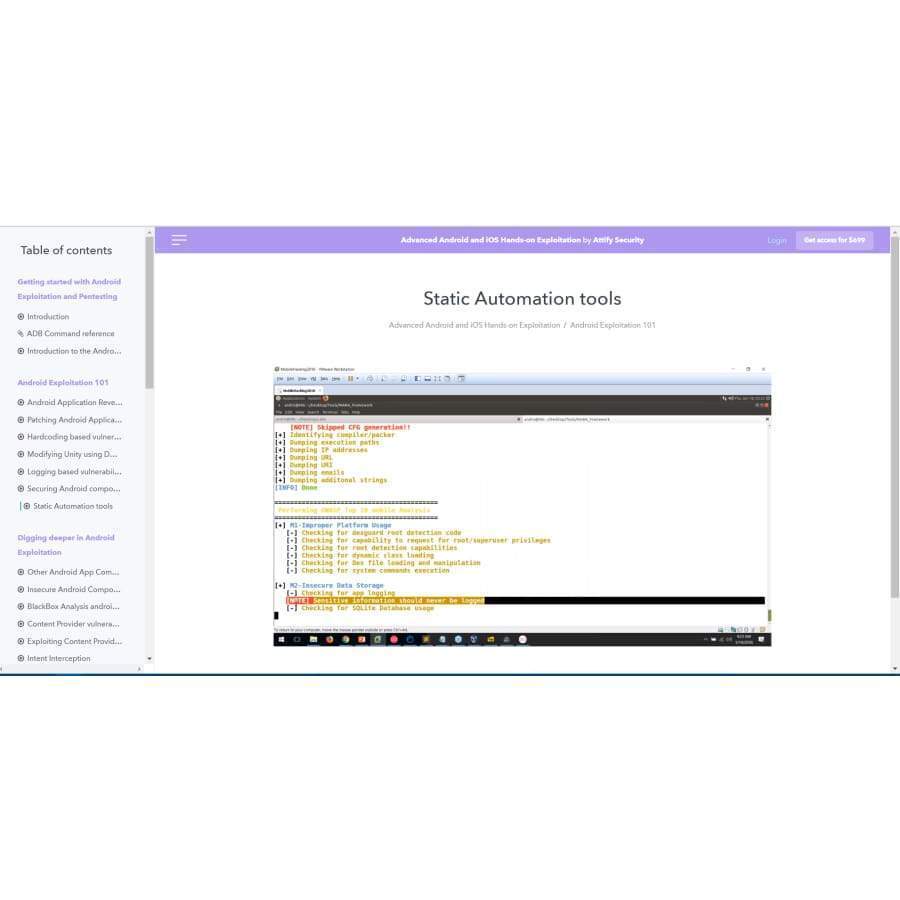
- Static Automation tools
Digging Deeper in Android Exploitation
- Other Android App Components
- Insecure Android Components
- BlackBox analysis of an Android app
- Content Provider vulnerabilities
- Exploiting Content Providers
- Intent Interception
- Exploiting Broadcast Receivers
- Sniffing Broadcast Receivers and Deeper app analysis
- Drozer Scripting
- Android Backup based vulnerabilities
Runtime Analysis and Exploitation
- What is Hooking?
- Introduction to Frida
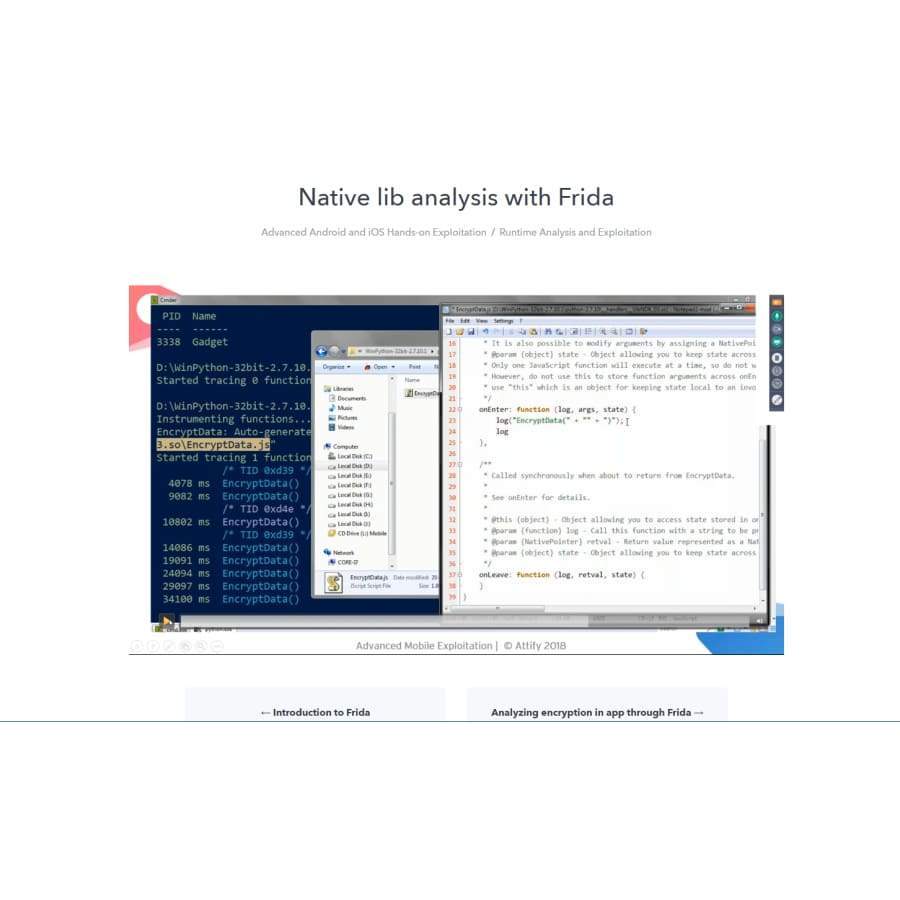
- Native Library analysis using Frida
- Analyzing encryption in app through Frida
- Advanced Frida Exploitation
Network Traffic Analysis in Android
- Getting started with Network analysis in Android
- Webview based vulnerabilities
Getting started with iOS Security
- Introduction to iOS Security
- Binary analysis for iOS
- Looking inside an iOS app
iOS App Exploitation
- Exploiting iOS Local data storage
- Digging deep into iOS Local data storage
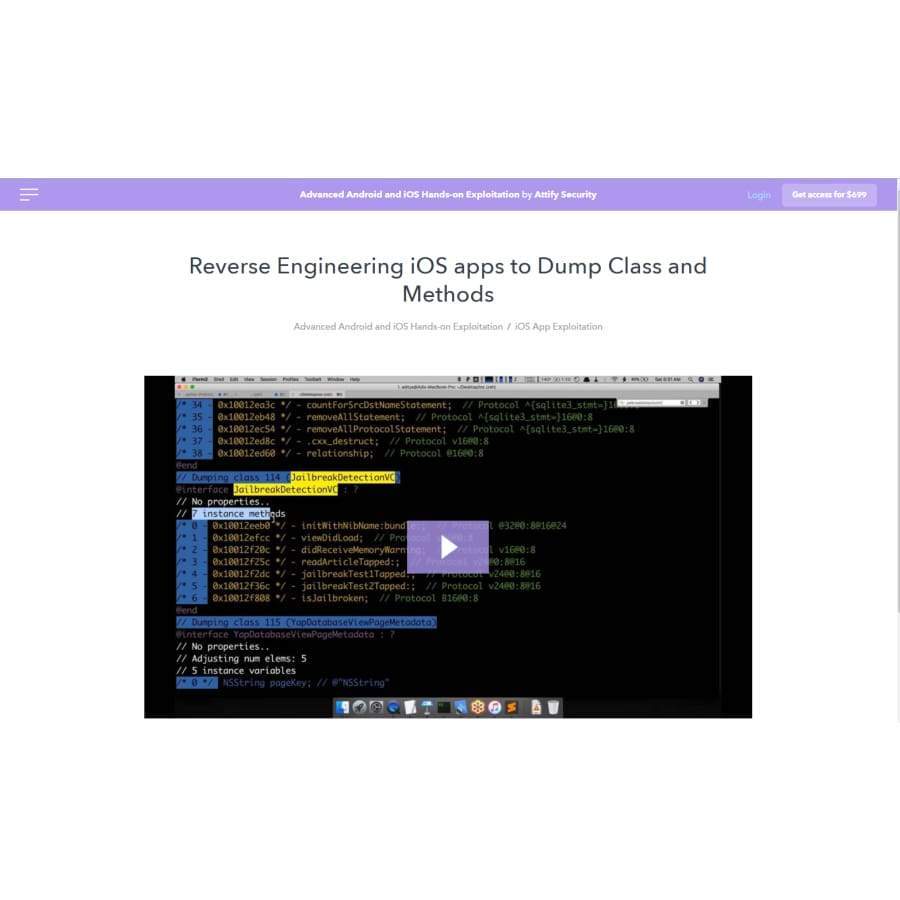
- Reverse Engineering iOS Apps to dump class and methods
- Decrypting iOS binaries
- Traffic analysis for iOS
- Runtime manipulation in iOS
- Additional tools
- Note: [CONTENT CONSTANTLY UPDATED] - You will get continuous access to the latest Mobile Exploitation training course material
All the above-mentioned topics are taught with extremely hands-on lab-based practical sessions.
WHAT STUDENTS WILL BE PROVIDED WITH
- Attify's Mobile pentesting VM
- Lab reference material and handouts
- 400+ slides (PDF Copy)
WHO CAN ATTEND THIS COURSE
- Mobile Security Enthusiasts
- Mobile application developers and Penetration Testers
- Anyone wanting to start in mobile application security
WHAT STUDENTS WILL BE REQUIRED WITH
- Free 25GB disk space with minimum 4 GB RAM
- Jailbroken iOS device (if you would like to perform iOS Exploitation)